How to Onboard Users to MeshDB
These instructions are for creating administrator console access for human users. For automated systems, see How to onboard applications to MeshDB
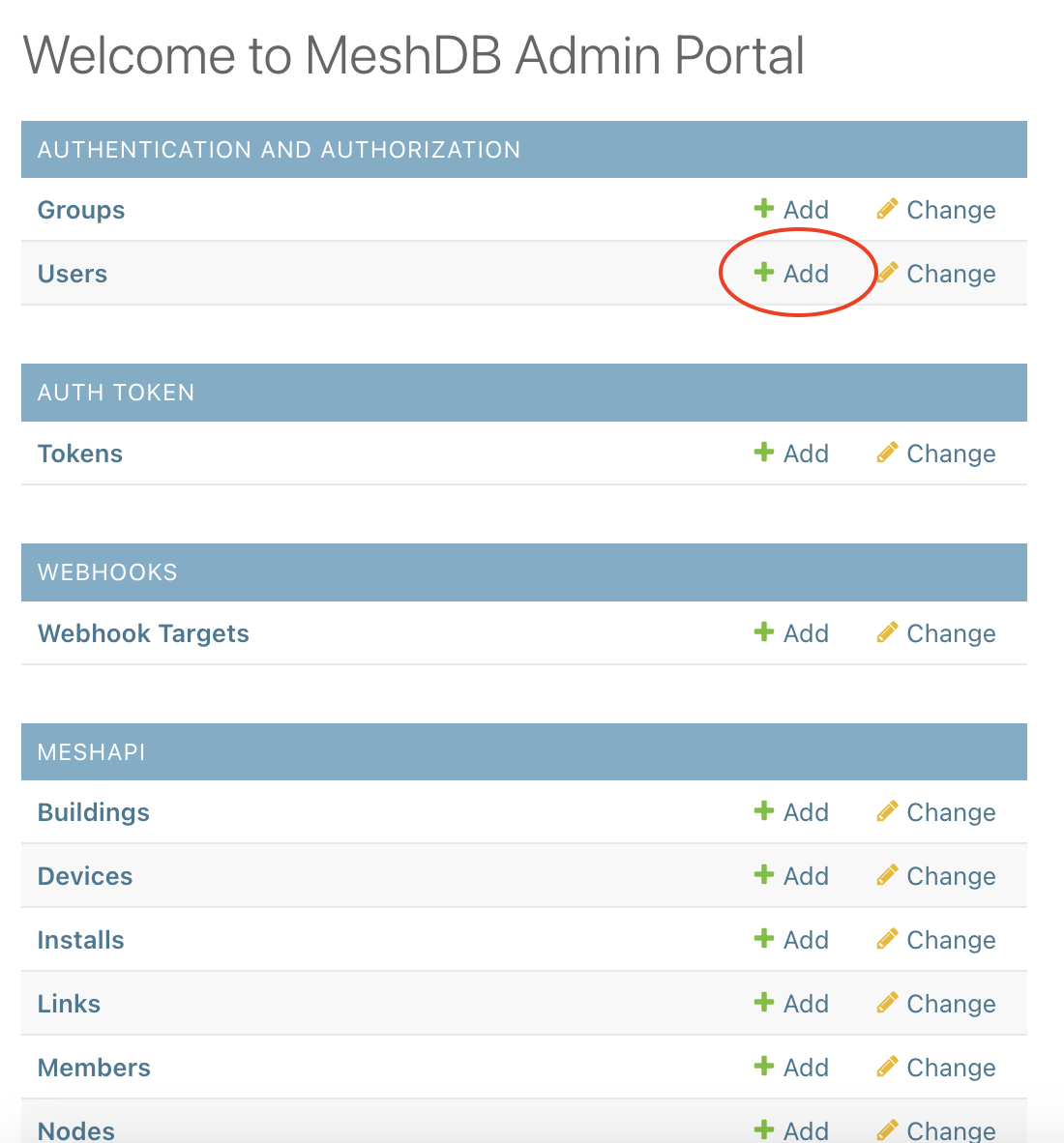
Adding a new user for admin console access
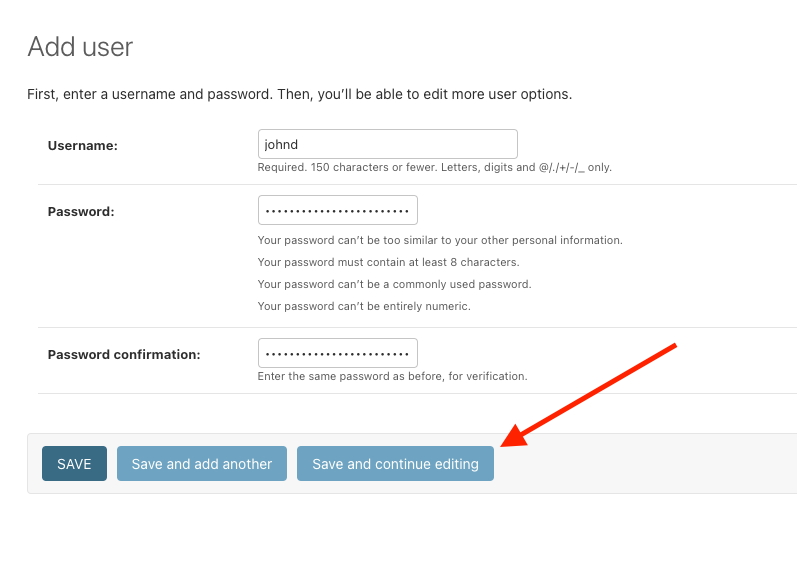
Every individual person should receive their own unique user object. User objects should not be shared among multiple volunteers. We have established an informal convention of using the volunteer's first name followed by their last initial. For example if the volunteer's name is John Doe, we would create their username as johnd. For the password, enter something secure, like a random password generated by your browser. Save this password and send it to the volunteer over slack (and encourage them to change it immediately using the link in the top right).
Click Save and continue editing to proceed to the full user editor
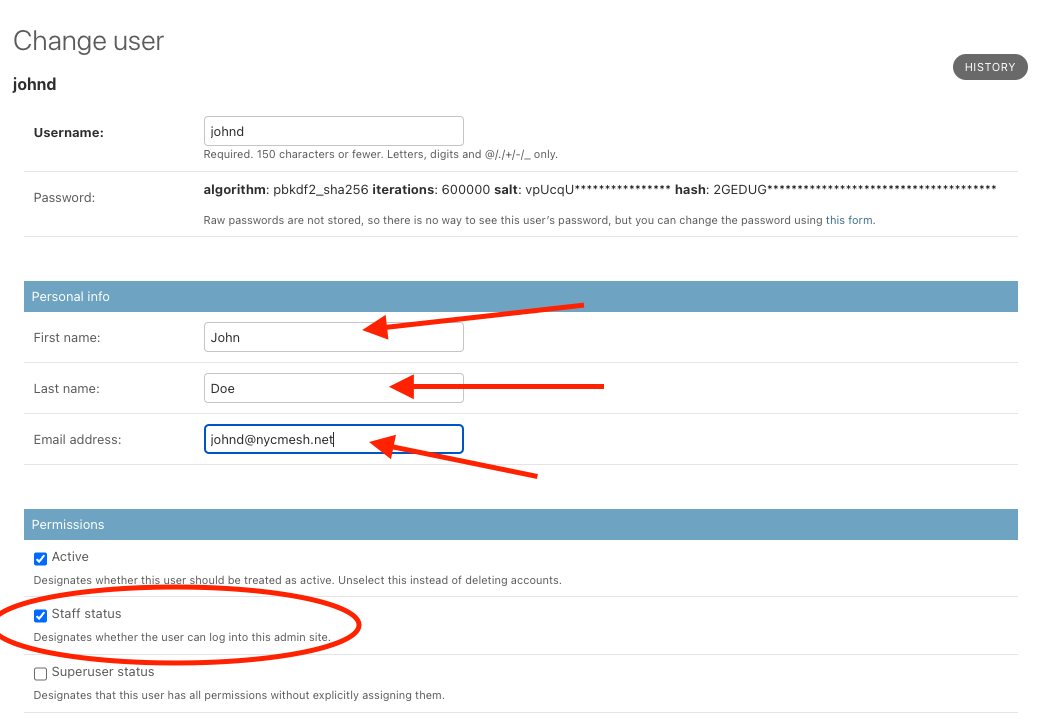
Here, set the volunteer's first and last name and email (if available). Then enable Staff status, which allows them to log in to the admin site.
Email address is not a required field. However, if you do not set an email address for the user, they will not be able to utilize the "Reset my Password" feature. So it is recommended that you set an email for all users
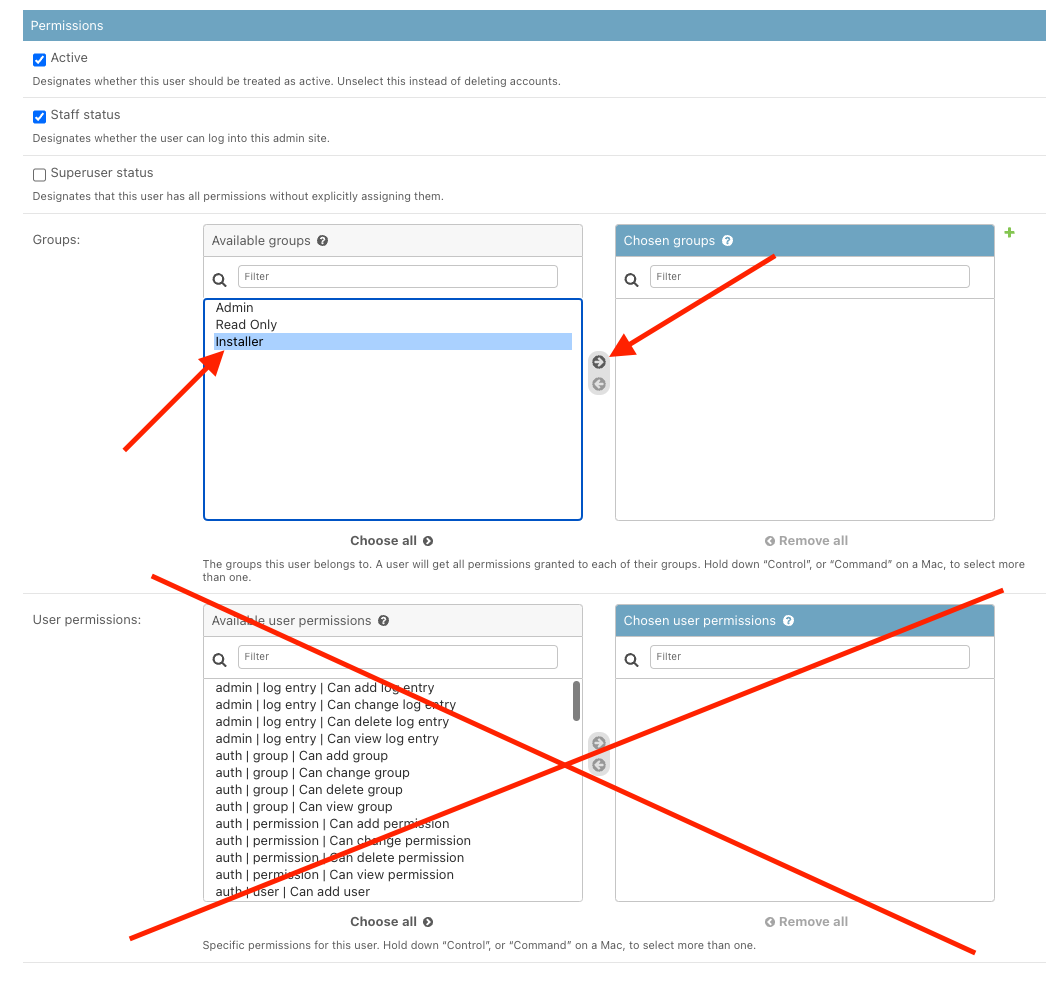
Finally, you need to add the new user to the appropriate group based on their needed permissions. The following table summarizes the difference in permissions between the various groups:
| Group | Permissions | Example User |
| Read Only | View-only permissions to all MeshDB core data such as Member Contact info, install details, buildings, etc No access to authentication information such as lists of MeshDB users or API tokens |
A junior installer |
| Installer | All permissions from Read Only, plus the ability to edit all MeshDB core data (buildings, install details, member contact info, etc.) but no permission to add or delete these objects No access to authentication information such as lists of MeshDB users or API tokens |
Install leaders |
| Admin | Full access to every table in the the core MeshDB database. Add, Edit, Delete permissions on these tables. Full view access to all tables, including authentication related information: Groups, Users, API Tokens. Ability to create and modify users. No access to modify the underlying structure of groups or add new ones. |
Mesh administrative staff |
| Superuser | Full access to do anything in the application. Bypasses all permissions checks, for safety reasons, this should only be applied to devs working on the maintenance of MeshDB itself The main thing this unlocks is the ability to modify the structure of the group permissions themselves, which should not be done lightly |
MeshDB Core Devs |
Do not grant permissions directly on the user object. Add the user to the appropriate group instead. Since the permissions are cumulative, a user should only need to be in a single group. To reduce confusion, this is strongly recommended.
Add the user to the appropriate group and save

No comments to display
No comments to display